Bugs Discovered
This page highlights security vulnerabilities and bugs we have discovered, including those reported through bug bounty programs and responsible disclosure to vendors, acknowledged by Google with a bug bounty, $500.
Misinforming Users: Location Permission Misleading in Wear OS
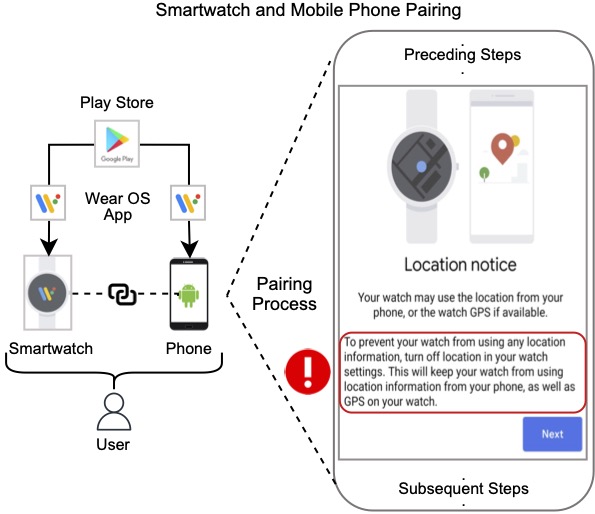
We discovered that the location permission prompt shown during the pairing process on Wear OS 2 misinforms users. When a user installs a fitness tracking app that requires location permission on both the wearable and its companion app, the system prompt suggests that location data will only be used on the wearable. However, even if the user denies location permission on the phone, the companion app can still access and transmit location data from the wearable to the Internet, misleading users about their privacy.
Impact:
Users may believe that denying location permission on their phone prevents any location data from being transmitted, but due to cross-device sensitive data flows, the data remains accessible and can be sent from the wearable. This undermines user consent and privacy expectations.
Technical Details:
- The location prompt during the pairing process (see Figure 1 above) does not accurately reflect the data flow between devices.
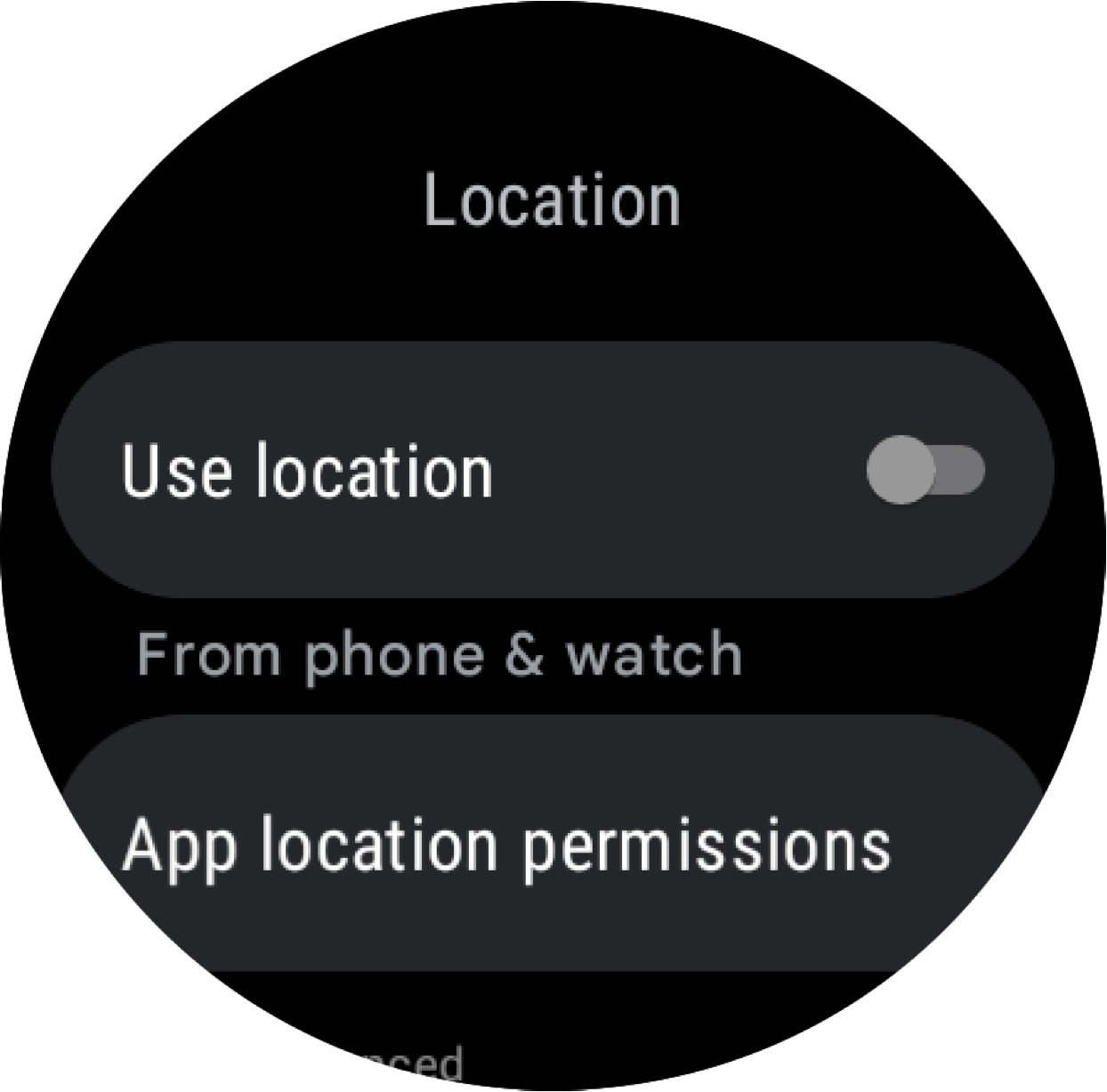
- Even after revoking location permission on the phone (see Figure 2 below), the wearable can transmit location data via Bluetooth or Wi-Fi.
- We developed a proof-of-concept app demonstrating this issue, and Google confirmed the finding.
Disclosure & Outcome:
We responsibly disclosed this vulnerability to Google, who acknowledged the issue and awarded us a bug bounty.
Update in Newer Wear OS Versions:
Android & Wear are working on a platform-level solution highlighted by our paper. For the updates in the newer version, please see the official Android developer documentation.
We discovered that the location permission prompt shown during the pairing process on Wear OS 2 misinforms users. When a user installs a fitness tracking app that requires location permission on both the wearable and its companion app, the system prompt suggests that location data will only be used on the wearable. However, even if the user denies location permission on the phone, the companion app can still access and transmit location data from the wearable to the Internet, misleading users about their privacy.

Figure 1: The location prompt shown on Wear OS 2 at the pairing process misinforms the users.
Impact:
Users may believe that denying location permission on their phone prevents any location data from being transmitted, but due to cross-device sensitive data flows, the data remains accessible and can be sent from the wearable. This undermines user consent and privacy expectations.
Technical Details:
- The location prompt during the pairing process (see Figure 1 above) does not accurately reflect the data flow between devices.
- Even after revoking location permission on the phone (see Figure 2 below), the wearable can transmit location data via Bluetooth or Wi-Fi.
- We developed a proof-of-concept app demonstrating this issue, and Google confirmed the finding.

Figure 2: Location permission toggle on the smartwatch.
Disclosure & Outcome:
We responsibly disclosed this vulnerability to Google, who acknowledged the issue and awarded us a bug bounty.
Update in Newer Wear OS Versions:
Android & Wear are working on a platform-level solution highlighted by our paper. For the updates in the newer version, please see the official Android developer documentation.
